Uber is the latest prominent organization to fall victim to prompt bombing, a social engineering tactic hackers use to gain access to a company's systems. This is not the first time, and certainly won't be the last time that we see an organization compromised by this type of attack. Cisco, Microsoft, and Okta are some of the most recognizable names to have been breached through prompt bombing within the last year.
Free Uber DFIR report courtesy of @hacker_ pic.twitter.com/RTsub1OjAE
— vx-underground (@vxunderground) September 16, 2022
While in these situations, it is easy to place blame. The reality is that an attack of this nature could happen to almost any organization. The volume of these types of social engineering attacks has rapidly increased– even within the past year. Attackers are getting smarter, tools are becoming more sophisticated and accessible, and hackers are documenting and sharing what works and what doesn’t.
Uber, what you need to know, the thread.
— Kevin Beaumont (@GossiTheDog) September 16, 2022
1) pic.twitter.com/CXU75bqrZU
In the case of Uber, the hacker not only spammed the employee with push notifications for over an hour, but, when that didn't yield quick enough results, resorted to using WhatsApp to contact them. From WhatsApp, the attacker told the employee they were from IT and successfully convinced them to approve the push notification. Similarly to past breaches, the attacker was then able to add a new device for future MFA challenges.
Once the attacker had access to Uber’s infrastructure, they found a network drive full of Powershell scripts. One of those scripts contained the most dangerous credentials an organization has: an administrative account to Uber’s password vault.
Usually, these accounts would be protected with MFA. In this case, because a script was using the account, MFA was turned off. Best practice dictates that any machine-to-machine vault accounts would be extremely limited in scope. In this case, for convenience, the account had access to a wide variety of Uber’s other credentials. Ultimately, accounts for Amazon Web Services, Duo, Google, OneLogin, and others were compromised as a result.
Recent studies have indicated that nearly ¼ of all data breaches can be attributed to user errors such as the ones above. Whether it be a push notification approved in the middle of the night or misconfigured security settings, when human beings are in the mix, accidents will happen.
This breach was the perfect storm of two multi-factor failures back to back - one account was successfully compromised by social engineering, and the other was compromised because MFA was disabled.
At the end of the day, the reality is that social engineering and attacks of this nature are not going to disappear. For most organizations, it's not a matter of if they will be a victim of social engineering; it's a matter of when. Phishing kits and other social engineering tools have become commoditized, and the only way to protect your organization is to search for ways to safeguard against social engineering proactively. MFA is the perfect place to start.
A step strongly encouraged is for organizations to implement phishing-resistant multi-factor authentication. The OMB, in conjunction with the White House, issued a memo titled “Moving the U.S. Government Towards Zero Trust Cybersecurity Principles” in January that heavily focuses on the importance of phishing-resistant MFA.
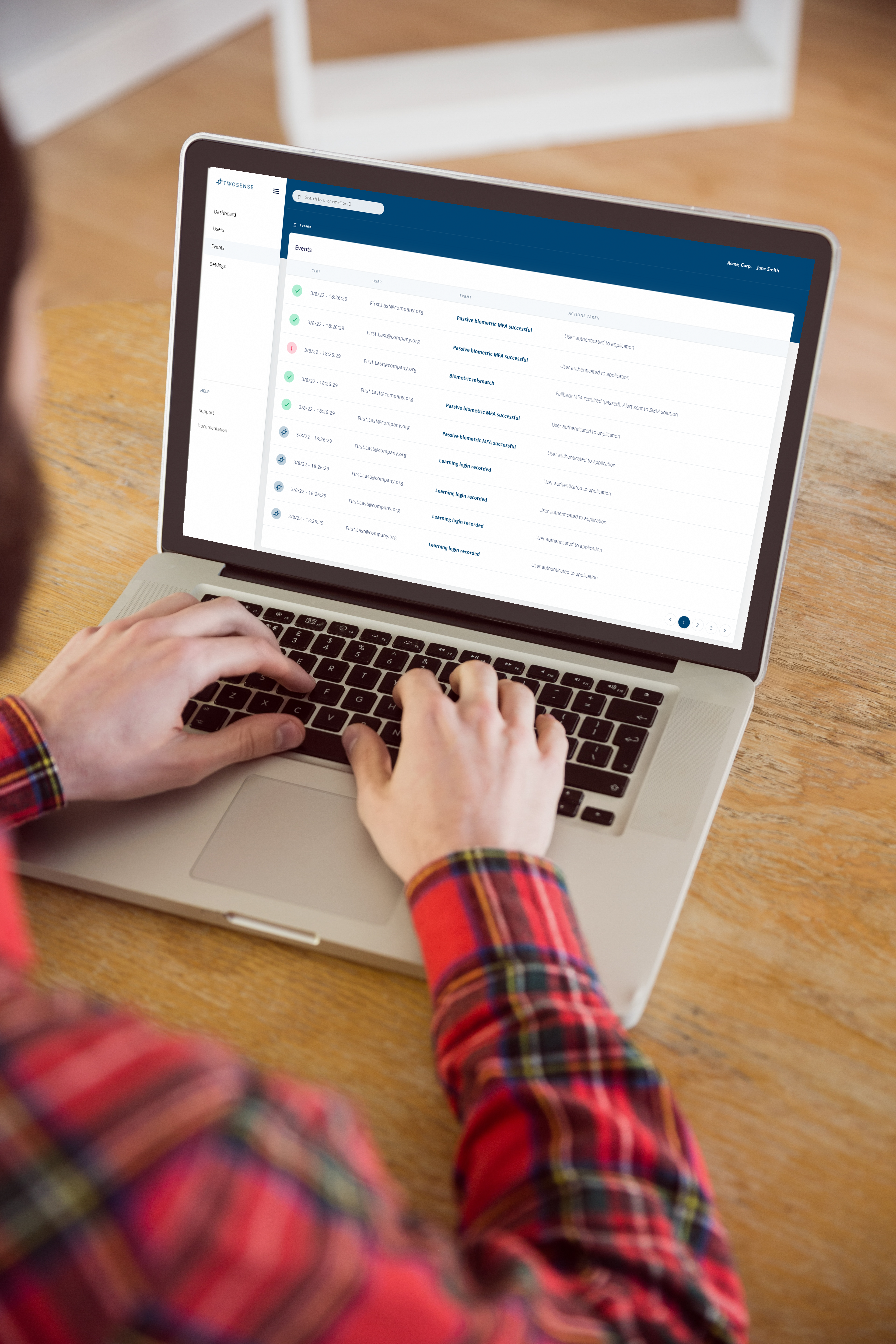
Twosense MFA uses machine learning which drives passive biometrics that can guarantee a user's identity continuously throughout the day. With Continuous MFA, the user’s recent behavior is continually compared to their behavioral biometric model. This means that multi-factor checks are being performed on users consistently throughout the day instead of waiting for the moment the users authenticate to an application.
Behavioral biometric MFA is the only solution capable of checking users' identities hundreds of times each day without requiring any participation from the users. Since there are no keys or codes that can be handed to an attacker in the event of a phishing attempt, it is completely phishing-proof. Developed in partnership with the United States Department of Defense, Twosense MFA makes it easier for organizations to defend against phishing attacks. With 3 simple steps, admins can deploy MFA everywhere, on every app, all the time.