2020 was undoubtedly an eventful year for the trading platform Robinhood, and it appears that it is not going to end any differently. On November 3rd the company announced that it had experienced a data breach that impacted 7 million users, with severity and types of data compromised varying across multiple groups of customers.
The most significant part of the breach leaked email addresses for roughly 5 million of the platform’s customers, with full names of 2 million. The same statement from Robinhood indicated that 310 customers may have had full names, dates of birth, and zip codes leaked, with an additional 10 customers having had “more extensive account details” compromised.
Robinhood's statement said that the breach has since been contained, law enforcement has been informed, and the party responsible for the breach demanded payment in an extortion attempt. Robinhood's chief security officer, Caleb Sima, said in the company's statement "As a Safety First company, we owe it to our customers to be transparent and act with integrity."
According to several outlets like Vice, the hackers behind the breach got access to an internal tool that presented them the option of tampering with user accounts, including removing specific users’ multi-factor authentication protections. The news only further highlights the potential risks that hackers can pose to organizations beyond simply compromising user data. Robinhood told Motherboard that it does not appear that the hackers made any changes to customers’ accounts based on their internal investigation.
The screenshots of the tool, which were provided to Motherboard by an individual who presented themselves as a proxy for the hackers, also show buttons for logging users out of their account, adding a trusted device, and blocking certain sessions from accessing the Robinhood account entirely, indicating that this particular breach could have been much worse. The screenshots also show that hackers could view users’ sensitive information, such as account balances and trades.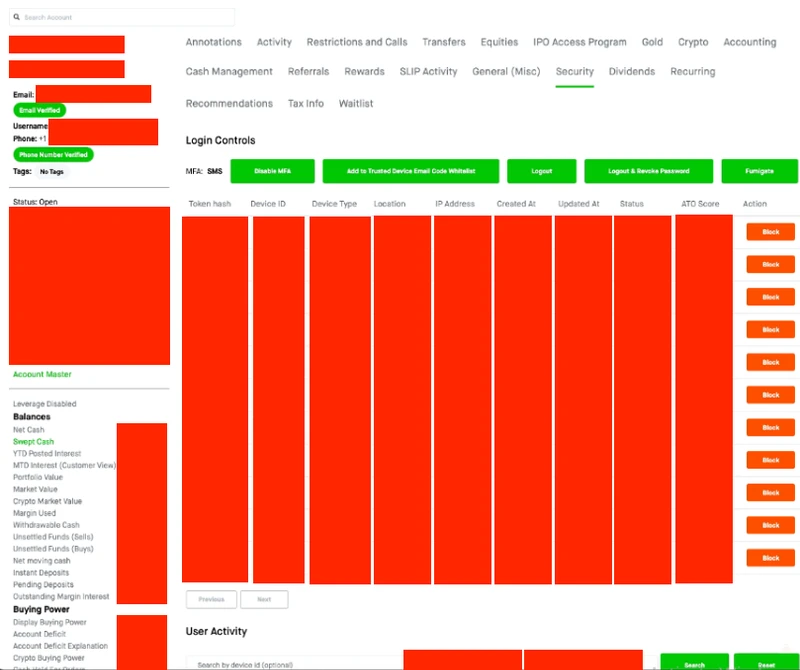
Companies often have internal tools for employees to make changes to customers’ accounts, troubleshoot, or resolve customer service issues but without the right security in place, hackers can in turn gain access to those tools and sometimes even leverage them in their favor.
The hack started with a phone call to Robinhood’s customer support, according to the statement that was released. The hacker relied on social engineering to convince an employee to provide "access to certain customer support systems," Robinhood said, circumventing all of the security and access control systems. Social engineering occurs when hackers use psychological manipulation to trick users into making security mistakes or giving away sensitive information. Social engineering depended on human error rather than security vulnerabilities, and given that 24% of data breaches are caused by human error, you can understand why this method is increasingly popular for hackers.
This is yet another breach that reinforces the importance of being able to validate a user’s identity without user input. When security systems are set up to make the user responsible for authenticating themselves, it leaves significant room for breaches and human error, as credentials for SSO/MFA can be stolen, devices can be stolen or lost, all of which leaves data vulnerable. Had Robinhood implemented continuous authentication and passive biometrics into their internal tools security protocols, they would have been much more difficult to hack into and could have prevented the breach from occurring at all.
If you are concerned that your data may have been compromised in the Robinhood breach you can visit Have I Been Pwned to query if your information has been leaked.
- Blog
- Robinhood Breach Once Again Reminds Us Why MFA Alone Is Not Enough
.jpeg)
Robinhood Breach Once Again Reminds Us Why MFA Alone Is Not Enough
- Multi-Factor Authentication
- Data Breach
- Passive Biometrics
- Continuous Authentication
- November 23, 2021
- 3 mins read
More from the Blog
October 22, 2025
The MFA Mandate No One’s Ready For The HIPAA Security Rule is being overhauled for the first time in nearly two...
December 18, 2023
In the rapidly evolving landscape of cybersecurity, the need for robust authentication measures is paramount. As BPOs &...
October 26, 2021
Every OneLogin single sign-on instance allows you to directly decide how many factors to challenge users with, and how...
Subscribe Here
We will never share your email address with third parties.


.jpeg)