Breaking news of data breaches has become so regular, that oftentimes unless it affects you immediately it can be easily overlooked. The Thingiverse breach is just one of many that remind us why maintaining security infrastructure is not only critical, it is paramount.
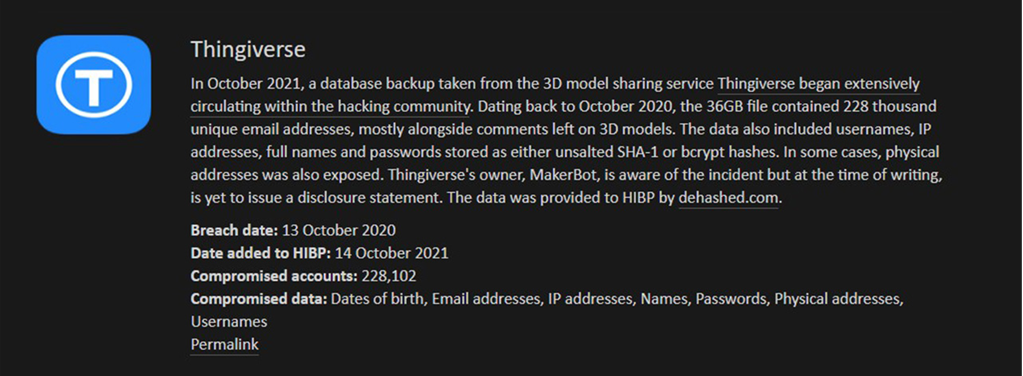
Former MakerBot employee and current Twosense engineer TJ Horner analyzed the data and recently spoke with Jeremy Kirk about some of the information that they found, and that article can be found here. Contrary to the information being shared by Thingiverse, TJ says that the breach likely affected more than 2 million people whose usernames were leaked. The breach also included OAuth tokens, which may also give hackers access to the video feeds of MakerBot 5th Gen printers and later models. Troy Hunt, creator of Have I Been Pwned says his website updated 10,646 users who have been affected by the breach, but that it could have exposed 228,000 unique email addresses as opposed to the “less than 500” that Thingiverse claims. This does not only raise concerns about transparency but causes many to wonder what the actual scope of the 36GB MySQL data stolen is. An additional concern that this breach put a spotlight on is the importance of infrastructure maintenance. According to Jeremy Kirk’s article, some critics alleged that the site's infrastructure has not been kept sufficiently updated. This particular breach occurred because someone at MakerBot made a backup of the database to a public Google Cloud Storage Bucket. The data then turned up on a well-known forum for buying and selling data breaches and included email addresses, IP addresses, usernames, DM’s, mod logs, and even full names and physical addresses. This is not the first time that MakerBot’s security has been criticized. Kirk's article goes on to explain that security experts have warned that the SHA1 hashing algorithm should not be used to handle passwords because it is relatively easy to brute-force the hashes it generates and recover plaintext passwords. This left passwords vulnerable to exposure. While MakerBot has not publicly acknowledged that OAuth tokens got leaked, the tokens have since been invalidated, meaning the leak should pose no further risk. However, if you are concerned that your data may have been one of the many compromised, TJ created an online tool allowing people to go and look up if they may have been affected by the breach. You can click here to access the query tool.
Had MakerBot adhered to zero-trust principles, this could have easily been prevented. Zero Trust means that no one is trusted by default from inside or outside the network, and verification is required from every user trying to gain access to an organization’s resources. Zero Trust may sound complex, but adopting this security model can be relatively simple with the right technology partner.
This breach reinforces the importance of removing the user’s responsibility for interacting with security infrastructure. Current systems require the user to prove that they are in fact an authorized user, which leaves significant room for human error. PR reps told Tech Radar “an internal human error led to the exposure of some non-sensitive user data for a handful of Thingiverse users.”
Organizations that implement software that automates 2FA/MFA add a layer of security that cannot be faked. Passwords and devices can be stolen, tokens can be phished, but using passive biometrics to confirm identity cannot be fabricated. If MakerBot had automated their identity security, the unauthorized user would not have been able to access the mismanaged data and subsequently could have prevented that data from being sold online.
.jpeg)
.jpeg)

