The COVID-19 pandemic precipitated a massive and hurried shift to remote work, creating new attack surfaces as employees access resources remotely. Working outside the perimeter in new workflows made employees more vulnerable to Spear-Phishing attacks, even at the executive level (also known as Whale Phishing, or Whaling). Since the start of the pandemic, spear-phishing attacks have increased by 667% with lures related to the virus, capitalizing on employee fear, uncertainty, and doubt. The impact of even one successful spear-phish is catastrophic to the organization, leading to data leakage, ransomware, and even organizational death. The need for increased identity assurance for employees working outside of the office has risen sharply as a result.
SPEAR-PHISHING SUCCEEDS THROUGH HUMAN ERROR
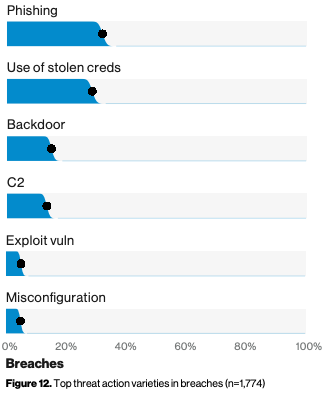
From the 2019 Verizon Data Breach Report, showing Phishing as the top threat, even pre-COVID.
In fact, 32% of breaches start with successful spear-phishing attacks. The anatomy of these attacks is fairly simple. An employee voluntarily and unwittingly grants their access to an attacker, usually fooled by lookalike logins or misdirection. While the benefits of multi-factor authentication are clear for increasing security, there’s even been a spate of attacks that circumvent two-step verification by convincing the user to execute the confirmation as well. At the bottom of this, the root cause is human error: all the security in the world doesn’t help if the user is able to unwittingly grant their access to an attacker. This is where continuous authentication can be a huge benefit to secure employees and organizations.
CONTINUOUS AUTHENTICATION IS AUTOMATED
Continuous authentication using behavioral biometrics is passive authentication that leverages technologies like keystroke dynamics and contextual factors for biometric authentication. This layers on top of existing remote access and single sign-on products to automate authentication that runs continuously for increased security with a better user experience. Automating MFA with continuous authentication not only improves security and the user experience, but it removes human error from the equation, and eliminates spear-phishing and whaling as an attack vector since the human is no longer involved in the authentication process. Computers are NOT fooled by website misspellings or fear-inducing emails, therefore automated authentication is not susceptible to those human-like mistakes.
CONTINUOUS AUTHENTICATION CAN HELP
Behavioral biometrics have been deployed successfully to combat account takeover and new account fraud in consumer-facing applications by companies like BehavioSec and BioCatch for years. Now, with recent advances, that technology has been adapted for continuous authentication in remote Enterprise workplaces. Starting with the US DoD, TWOSENSE.AI has created the first Enterprise product that continuously protects work-from-home employees with behavioral biometrics, for a better user experience that’s completely resistant to spear-phishing attacks. It layers on top of existing Single Sign-On and Multi-Factor Authentication technology to automate the challenge-response of day-to-day logins and make access useless to unauthorized attackers.
Reach out to us to find out how we can help your organization protect itself against spear-phishing and whale-phishing attacks, while greatly improving the remote employee user experience.Hello world!


.jpeg)
.jpeg)