Microsoft presented at RSAC in San Francisco this year and revealed some shocking figures. What they saw is that a whopping 1.2 million (0.5%) Azure AD enterprise accounts are compromised every month. Account compromise means that a malicious actor or script gains some kind of access to internal resources. While the goal is unclear, it could range from simply sending out spam, all the way to stealing secrets and escalating access.
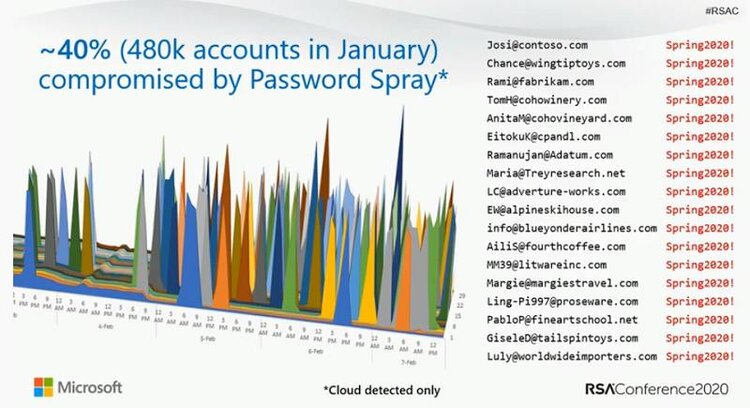
Microsoft’s RSAConference 2020 presentation showing 40% of accounts are compromised by Password Spray attacks per month
In trying to figure out how these attacks happen, Microsoft revealed that 40% are password spray attacks. In this case, attackers use a database of usernames and try logging in with statistically probably passwords such as “p@ssw0rd” or “letmein”. The other 40 percent of these attacks are due to password replay, where attackers mine data breaches assuming that many people will reuse passwords and enterprise passwords in non-enterprise environments. The last 20% or so is due to other attacks such as spear phishing.
The recurring theme is that in 99.9% of these cases, organizations didn’t have Multi-Factor Authentication (MFA) enabled. MFA requires a user enter one additional identifier when logging in or accessing a system, whether that be a code sent to another device (SMS, E-mail, TOTP etc.) or a security key such as FIDO2. What’s even more surprising is that even though MFA stops 99.9% of these attacks, only 11% of Microsoft’s Enterprise accounts have it enabled! For a lot of these organizations, enabling MFA is as simple as toggling a switch in the account settings. So why haven't organizations enabled MFA if it’s that simple?
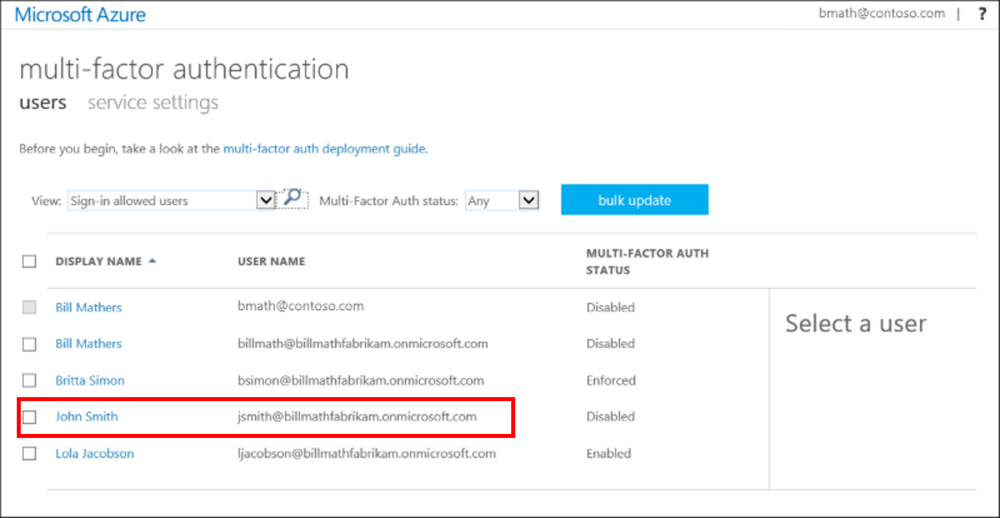
Microsoft Azure AD settings, where teams can enable MFA for specific users
The resounding answer is that enabling MFA causes user friction for an organization. In order to enable MFA, organizations have to disable legacy authentication (which only requires a username and a password) and use more modern authentication such as OAuth 2.0. However, in doing so, it may break or limit access to applications, heavily disrupting business flow. Microsoft actually tested this internally for a sales team and 60,000 users were locked out of an extremely important application, causing a serious business disruption referred to as a “severity 1” meltdown within the company. “In the middle of the night we started getting calls” said the identity and access security team. As a result, Microsoft acquiesced to the demands of the users rolling back the policy, and leaving themselves vulnerable to a data breach to make users happy and allow them to get back to business. While this is just one case, there are many cases in which an organization enables MFA and runs into problems with usability and user friction.
As we’ve seen time and time again, when it comes to the happiness of the users, cybersec/infosec professionals are at the mercy of the organization yet responsible for all the risk of a data breach. Despite knowing of security vulnerabilities and how to address them, the employees’ user experience was prioritized. If an organization enables MFA, there's a high chance they may encounter user friction, but the bottom line is that any organization allowing 0.5% of their accounts to be compromised per month or more is a long way from where it should be regarding security. So what can an organization do to enable MFA without adding any user friction?
One way is to make sure that when enabling MFA, there is as little disruption to business flow as possible. At TWOSENSE.AI our mission is to make your MFA experience as frictionless by using continuous behavioral biometrics. Using your existing hardware and software login workflows, TWOSENSE.AI automates the response to MFA challenges for your users invisibly in the background. We can automate up to 95% of incoming MFA challenge responses, saving each user an average of 1.5 hours per month.
Find out how TWOSENSE.AI can help you enable MFA at your organization without interrupting business flow.