IS 2FA REALLY THAT SECURE?
In recent news, a Chinese government-linked hacker crew, APT20, was seen going through multi-factor authentication (MFA) implementations, bypassing that security to gain access to otherwise secure infrastructure, and had used it for weeks. Surprisingly, the second-factor authentication (2FA) bypass didn’t take advantage of the usual cell network weaknesses to receive 2FA texts, it bypassed hard RSA time-based one-time-password (TOTP) access. It’s unclear how exactly this happened, but the research hypothesizes that the attackers gained access to a seeded instance of the TOTP generators software, and were then able to generate their own correct TOTPs. The crew used this vulnerability to target managed service providers (MSP) and Government organizations across Europe and the Americas.
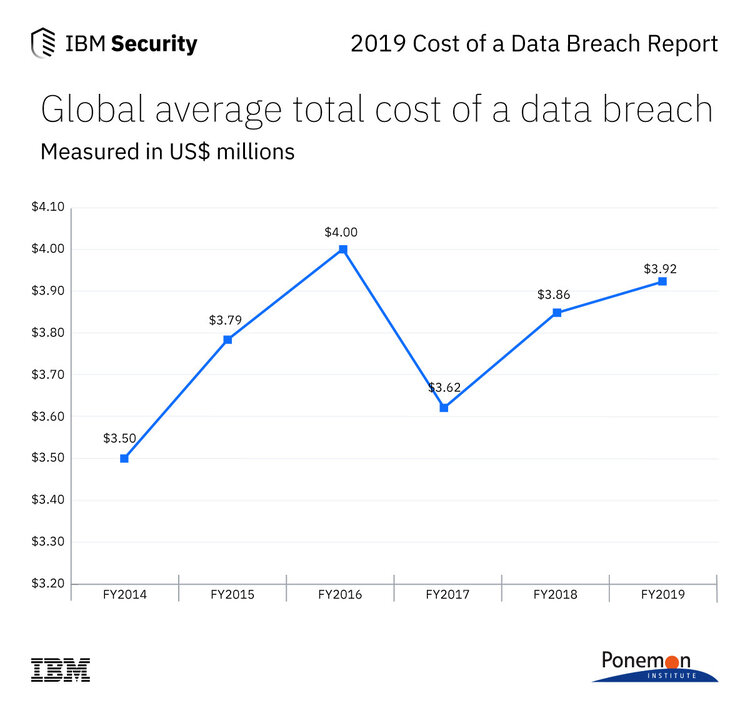
Global average total cost of a data breach based on a study conducted by Ponemon Institute and sponsored by IBM Security
While the complexity of this MFA compromise is surprising, these types of compromises are becoming ever more frequent. One of the reasons why this is so concerning is because the cost of a single successful attack reached an average dollar amount of $3.92M in 2019. The FBI recently put out a warning that attackers were hacking through basic MFA and documenting how these attacks occur in the wild. In theory, these compromises should be eliminated through a Zero Trust security posture, which encourages systems to adopt the approach of assuming every access request is unauthorized until proven otherwise, an approach first proposed by Google called the BeyondCorp paradigm.
While this approach can eliminate 82% or more of compromises, the impact to the user of repeated MFA challenges can be unacceptable. In fact, Microsoft also notes that less than 10% of Enterprises have adopted MFA. The main reason for this is the non-monetary cost to orgs of MFA, such as user annoyance from MFA challenges, and the helpdesk costs of supporting that process. For example, recent developments have demonstrated that Enterprise users will take any measures available to them to disable MFA on their accounts regardless of the security consequences. Enterprises often mitigate that friction by relying on second-factor authentication or 2FA, checking that the devices are correct rather than the user. This can often lead to complications where the system trusts a software or hardware instance as a proxy for the user to save user effort. In this case, the TOTP-generating piece of software was trusted even after compromise, meaning it could be used in the absence of the authorized user to give the attackers access at will. According to the FBI’s notice, the path forward is to deploy behavioral authentication as a continuous biometric layer on top of MFA.
Continuous behavior-based biometrics solve this problem in two ways. First, behavior-based biometrics eliminate the friction of authentication from the user experience, since there is nothing extra the user needs to do. Second, biometrics eliminate the need to rely wholly on trusting second factors, such as devices and software instances which are susceptible to compromise as was the case in this instance.
TWOSENSE.AI provides continuous biometric authentication as an MFA addon for Enterprise single sign-on environments. It is a drag-and-drop integration that seamlessly removes MFA challenges from the user experience while protecting employee identity with continuous biometrics to drastically improve security.
See how your organization can get better security with a better experience by signing up for a demo today!
Try It Free
-1.jpeg)

.jpeg)