As organizations look for any edge to improve their security posture, number matching is poised to become one of the next most widely adopted security features. Microsoft Authenticator will roll out number matching as a default for all organizations starting in February 2023. Number matching as a factor is something that has been encouraged by Cybersecurity and Infrastructure Security Agency (CISA) to help reduce accidental approvals, phishing, and limit fallout from MFA fatigue– a tactic many industries felt the impact of this year.
The number-matching feature works by presenting users with a number when they respond to an MFA push notification using the Authenticator app. Users would then be required to type that number into the app to complete the approval as seen in the image below.
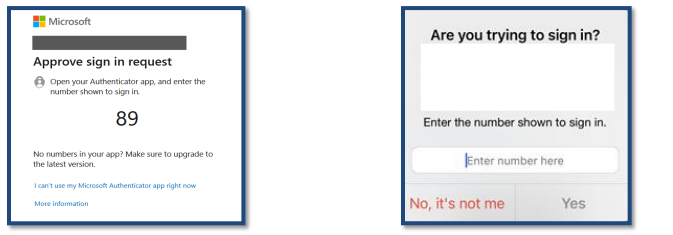
An MFA fatigue attack, or prompt bombing, is when threat actors deploy an endless barrage of push notifications to a target mobile device. This tactic relies on annoyance and inconvenience. The attackers hope that the high volume of push notifications will trick or annoy the user into approving an MFA push notification or accidentally doing so by trying to silence their device. Number matching helps here because it prevents the user from accepting 2FA for a sign-in attempt they can’t see with an extra verification step.
Industry experts like Dawud Gordon say 2022 was undoubtedly the year of the MFA bypass. This should not have come as a surprise. According to Okta’s State of Identity Security report, in the first 90 days of the year, Auth0 observed almost 113 million attacks against MFA. As MFA became standard practice for authentication, the need to bypass MFA increased rapidly.
Data shows that nearly one-quarter of all breaches can be attributed to user error, so it makes sense that organizations actively seek to implement every safeguard available. Couple what we know about user error with the fact that about one percent of users will always click on something, like a push notification– it's understandable why guardrails are needed when it comes to authentication.
While number matching is said to help safeguard against “accidental approvals” and MFA fatigue, implementing this feature means increasing security friction for an already taxed workforce. In addition to adding seconds to every MFA challenge response, number matching is not a safeguard against social engineering. If the user believes they’re doing the right thing, they can still be tricked into granting attacker access and phished for the correct number.
When it comes to identity security, the best defense is to implement solutions built on zero-trust principles and phishing-resistant solutions. Twosense Passive and Continuous MFA are phishing-resistant by design and prevent MFA bypassing by using passive biometrics to authenticate users.
With number matching, even though the end user is explicitly forced to enter a two-digit number to approve the access request, a threat actor could still social engineer a call with an employee. All it takes is one threat actor to convince one user that they are from the IT or Security team for them to get access to that two-digit number opening the door for an attacker. With passive biometric authentication, Twosense can stop these types of breaches in its tracks.
Twosense MFA deploys as an agent or window browser. In this scenario, even if the user gave a threat actor the two-digit code, the unauthorized use would immediately be flagged and remediated. Even if the attacker gains remote access to an active and authenticated session or phishes an active session token, the biometric mismatch would have been identified, and action could have been taken immediately.
It is understandable that organizations want to embrace security safeguards, and implementing solutions that both bolster security efficacy and reduce friction provides the most benefit across the organization.
To learn how you can deploy phishing-resistant, biometric, continuous MFA, schedule your demo here.