A White Paper To PCI DSS v4.0 Multi-Factor Authentication

Table of Contents
- Introduction
- Implementation Timeline For PCI DSS 4.0
- Section 1: An Overview of Relevant Changes in Requirement 8
- Section 2: MFA For Network Access
- Section 3: Required 15-Minute Timeouts
- Section 4: 3-Month Password Rotations
- Conclusion
Introduction
Contact centers are stuck between a rock and a hard place: PCI DSS compliance and the available technology. Meeting the required standards is difficult when the current MFA solutions do not meet the requirements.
PCI DSS v4.0 will take standard in March 2024, and requirements are stricter than in 3.2.1. However, agent identity security is a priority for BPO customers. As such, organizations should not wait until the last minute to ensure their identity security systems and policies are up to PCI DSS v4.0 standards. Organizations must review the Section 8 requirements and develop a plan to meet them before March 31, 2025.
Cutting corners on compliance is not an option; the security requirements mandated by PCI and NIST are critical when it comes to securing cardholder data environments. In 2022 contact centers saw a significant increase in cyber attacks, with roughly 4,100 publicly disclosed data breaches occurring and 22 billion records being exposed. Last year some of the most prominent names in the BPO space experienced data breaches, most of which occurred as the result of MFA fatigue.
As hackers’ technologies and strategies become more sophisticated, the PCI authentication requirements have evolved to meet them. Thus, maintaining best practices and utilizing the tools and guidance provided by the PCI SSC is critical for compliance and an effective security posture.
In this white paper, our team will discuss the impacts of these new requirements on BPO contact centers and their customers regarding multi-factor authentication and agent identity security.
Implementation Timeline For PCI DSS 4.0
Take a look at when PCI v3.2.1 retires and PCI v4.0 goes into effect.
In March 2022, the PCI Security Standards Council (PCI SSC) released version 4.0 of the PCI Data Security Standards (PCI DSS). Upon the release of the updated guidance, the PCI SSC also published an implementation timeline for when organizations are expected to transition to the new PCI v4.0 standards and when the new requirements will become mandatory.
There has been a lot of confusion about the timeline for changes since some requirements are future-dated. Most changes specific to Requirement 8 will go into effect on March 31, 2025. However, due to the complexity of the new MFA requirements, organizations should not wait until the last minute to ensure their identity security systems and policies are up to PCI DSS v4.0 standards.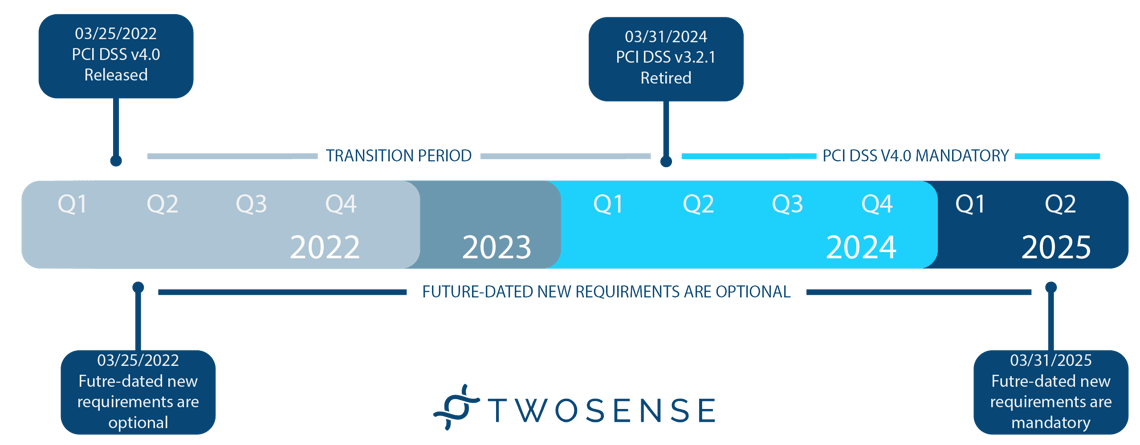
Timeline based on a graph from PCI DSS v4.0 At-a-Glance, 2022 PCI SSC
March 31, 2024 -PCI DSS version 3.2.1 retires
The PCI v3.2.1 standards will be retired on March 31, 2024.
March 31, 2024 - PCI DSS version 4.0 takes effect
After that, PCI v4.0 takes full effect, except for a few specific requirements, which are future-dated to one year later. Organizations are encouraged to start using the PCI v4.0 standards immediately but are not required to follow the new standards until March 31, 2024.
March 31, 2025 - Future-dated requirements in PCI DSS v4.0 become mandatory
Future-dated requirements are prescribed as best practice until March 31, 2025. All future-dated requirements will be mandatory after March 31, 2025, and must be considered during a PCI DSS assessment.
There will be difficulties around password complexity and password rotations, and BPOs will be responsible for enforcing these requirements with customers and partners, which you can read about here.
Something to note is that while future-dated requirements are guidance until March 31, 2025, many customers and partners may demand it now and even more so after March 2024. It is in every organization's best interest to implement the new standards sooner rather than later.
It is important to note that organizations are not required to use the PCI v4.0 standard until March 31, 2024. Organizations may follow either the PCI v3.2.1 or the PCI v4.0 standards during the two-year transition period.
Until then, PCI Qualified Security Assessors can perform assessments using either the PCI v3.2.1 or PCI v4.0 standards if the QSA has already completed their PCI v4.0 transition training.
Section 1: An Overview of Relevant Changes in Requirement 8
What You Need To Know About Requirement 8 & MFA In Contact Centers.
On March 25, 2022, PCI DSS v4.0 was officially announced, and its implementation date is just around the corner. One of the major changes that will be seen in PCI 4.0 is an emphasis on multi-factor authentication (MFA). Requirement 8 experienced a significant overhaul, with every section containing entirely new additions. Last April, the Twosense team broke down many of these changes and what they mean for organizations, which can be found in the What You Need to Know About PCI DSS 4.0 blog.
There are, however, a few requirements that BPOs and their customers should be paying specific attention to because starting soon, BPOs will have to rotate agents’ passwords every three months (unless certain new requirement conditions are met), there will be an increase in MFA challenges to access systems, and cracking down on mandatory timeouts after 15 minutes of inactivity. This will be extremely challenging to manage, but Twosense’s one-of-a-kind software will make it a non-issue for BPO contact centers.
These sections include:
- 8.4.3 MFA is now mandatory for users (agents, admins, vendors, etc.) when accessing the network (e.g., a VPN connection).
- 8.4.2 Even after that first MFA, MFA is required again for each access request to the card data environment (CDE).
- 8.2.8 Session timeouts are now set at NIST-standard 15 mins, after which all of the above must be redone.
On top of that, there are new requirements for BPOs and service providers specifically, that become difficult without continuous identity controls:
- 8.3.10 Without continuous security posture evaluation, credentials will need to be rotated every three months.
- 8.3.10.1 Furthermore, if the agent’s credentials are managed by your customer, it is your responsibility to see to it that your customer rotates these credentials every three months, again, unless you can implement a continuous security posture evaluation.
While compliance tends to be complicated to interpret, the primary goal of PCI 4.0 as it pertains to multi-factor authentication is clear: deploy MFA to everyone.
This means every individual –agents, vendors, and third parties– will be required to authenticate when accessing a VPN, again to access the CDE, and again for all
applications. An additional measure was added to clarify that completing an MFA challenge into any system does not mean you can forego authenticating into the
others.
It’s crucial for BPOs and their customers to pay close attention to these requirements and to take the necessary steps to ensure they are on track to meet the new
compliance standards. Failing to comply with these requirements could result in customers churning out, hefty fines, and damages to an organization’s reputation.
Implementing MFA is critical in enhancing cardholder data security and reducing the risk of data breaches and it is paramount for BPOs. With Twosense, contact
centers will be empowered to deploy secure, PCI-compliant solutions without adding unnecessary friction, which would be extremely challenging to do with traditional MFA.
Section 2: MFA For Network Access
PCI DSS v4.0 Requirement 8 leaves no room for doubt; everyone must have MFA in contact centers.
The pandemic pushed all businesses that could adapt to a work-from-home model, and contact centers were no exception. Initially, many were uncomfortable with
the work-at-home-agent (WAHA) model, mostly due to security concerns. Over time, compliance auditors and contact center operators found ways to meet in the
middle and make WAHA models successful. PCI 4.0 is bringing new scrutiny and requirements to agent security, which will throw a major wrench in the gears of new and existing contact center businesses, particularly for WAHA business models and especially for outsourced BPO contact centers. We’re going to look at why here.
Requirement 8.4.2 is where this white paper will begin. As discussed last week, while compliance tends to be dry and complicated to interpret, the PCI SSC has made its
position on MFA clear in PCI 4.0: deploy MFA to everyone, everywhere.
8.4.2 MFA is implemented for all access into the CDE.
“If an individual first connects to the entity’s network via remote access, and then later initiates a connection into the CDE from within the network,
per this requirement, the individual would authenticate using MFA twice”
This means every individual –agents, vendors, and third parties– will be required to authenticate when accessing a VPN, again to access the CDE, and again for
all applications. Furthermore, there is no exception for agents within a clean room environment: MFA is now required in the secure facility as well. An additional
measure was added to clarify that completing an MFA challenge into any system does not mean you can forego authenticating into the others. This means that even after that first MFA, MFA is required again for each access request to the card data environment (CDE).
8.4.1 Administrative access to the CDE cannot be obtained by the use of a single authentication factor.
If you are reading between the lines here, you know this presents one significant problem– security friction. This friction will only increase as requirements compound upon one another– which we will discuss in the next section.
Implementing these new standards will significantly increase agents’ time interfacing with MFA. Agents will be required to authenticate into their primary system or VPN, again to enter any cardholder data environments, and into every application required to perform their job.
This will be challenging from an implementation perspective but will also impact the bottom line. What used to be a single sign-on event for an agent to start a shift will now be a complex, multi-stage process taking considerable time. Furthermore, as we’ll talk about later in this series, this process will now have to be repeated several times throughout a single day. For every hundred agents, thousands of minutes each month will be spent on MFA challenges instead of significantly impacting shrinkage in a negative way. The more time agents spend authenticating into systems, the less time they can spend with customers. Also, as every IT practitioner knows, every interaction with authentication can result in a problem, and many more authentications mean many more help-desk tickets.
How do BPOs move forward in a way that will meet compliance standards and mitigate security friction? The solution is simple: deploy an identity security MFA
solution capable of invisibly authenticating agents in zero time without sacrificing security.
This is where Twosense can help contact centers. With behavioral biometrics Twosense can validate an agent’s identity and authenticate them not by what they’re
doing but by how they’re doing it, generating a level of trust for every interaction in the background. That trust score is then used to authenticate the user continuously throughout the day or flag suspicious behavior. Behavioral MFA authenticates on endpoints, web, and Single Sign-on, getting BPOs PCI 4.0 compliant with MFA everywhere and all the time.
Twosense Behavioral MFA is PCI 4.0 compliant and doesn’t require hardware. That means no enrollment is necessary, making deployment to agents simple. Once the Twosense agent is installed on each user’s machine– which is three easy steps– no further action is required.
Section 3: Required 15-Minute Timeouts
Security friction in contact centers will skyrocket without the right MFA solution.
With PCI v4.0 making it clear that multi-factor authentication is mandatory for everyone and all network access, it is important to consider how other updates in PCI Requirement 8 will impact security friction. One of the many new additions to PCI 4.0 is an alignment with NIST 800-63B guidance on 15-minute timeouts. In PCI 3.2.1, 15-minute timeouts were a recommendation but not a requirement. In PCI 4.0 Requirement 8.2.8 states:
If a user session has been idle for more than 15 minutes, the user is required to re-authenticate to re-activate the terminal or session.
The addition of the requirement for 15-minute timeouts is aimed at reducing the risk of unauthorized access to sensitive cardholder data. If an agent’s session has been inactive for more than 15 minutes, the agent must re-authenticate to reactivate the terminal or session. This is to help prevent unauthorized individuals from accessing cardholder data if an agent leaves their workstation unattended for an extended period, or their active session is somehow illegitimately accessed (e.g. session or token hijacking).
Implementing mandatory timeouts after 15 minutes of a user session being idle, compounded with other new requirements, will drastically increase the security friction agents experience daily. The most obvious disruption the implementation of 15-minute timeouts will have is on an agent’s workflow. It will significantly impact productivity if agents have to re-authenticate every 15 minutes, leading to frustration and a negative customer experience.
Depending on the authentication method being used, logging back into the system after a timeout will take additional time and effort for the agent. This can be particularly problematic when the contact center is experiencing high call volumes or long wait times for customers, as it can lead to increased handle times and decreased efficiency.
One complication is that the new PCI requirements have changed their view on what constitutes a session. It has been made clear that a VPN or network connection is one session, and the Card Data Environment (CDE) is another, each requiring it’s own multi-factor challenge for access, and each now expiring strictly after 15 minutes of inactivity. Furthermore, for agents connecting to multiple CDEs, each of those is regarded as it’s own session as well. Leaving one CDE unused for 15 minutes (for example if the tab or application is minimized) will require full MFA to re-initiate
that session, while stepping away from the machine for, say, a bathroom break, will require an MFA challenge to reconnect to the network, and another for every CDE reconnection.
Ultimately, the addition of 15-minute timeouts in PCI v4.0 will wreak havoc in contact centers attempting to maintain compliance with traditional multi-factor authentication solutions – for both agents and their supervisors. The solution to mitigating the impacts of these requirements is to deploy a multi-factor authentication solution that automates the MFA challenge response while continuously authenticating agents’ identities throughout the day.
It is crucial to note that without continuous authentication, automating MFA to combat 15-minute timeouts is impossible.
Twosense Continuous MFA is uniquely designed software for contact centers that does not require a mobile device, hard token, or additional training. Twosense creates a unique biometric profile for each user. Each model learns and adapts to changing behaviors to biometrically authenticate the user at every MFA challenge in an invisible way. The more behavior is observed, the more confident Twosense can be that
the user is who they claim to be. Continuous MFA validates the user’s identity and authenticates them not by what they’re doing but by how they’re doing it, generating a level of trust for every interaction in the background. That trust score is then used to authenticate the user continuously throughout the day or flag unauthorized access. Twosense solution can be deployed as an agent on each user’s machine– deployment is as simple as three easy steps that can be done in a single afternoon.
Continuous MFA ensures the correct agent is behind every keyboard, allowing agents to work frictionlessly throughout the day. Should an agent walk away from their station, share their credentials, or otherwise have their device or station compromised, Continuous MFA gives contact centers the security of knowing a behavioral mismatch will occur, ending the unauthorized user’s session immediately. We give BPOs better security overall that can be demonstrated to their customers.
Section 4: 3-Month Password Rotations
Password complexity and rotation have become stricter in PCI 4.0.
In contact centers, security is more important than ever before. Still, strict clean desk policies and the cost of hard tokens like YubiKeys have made multi-factor authentication (MFA) difficult to impossible to implement. For most contact centers, there has been a way to thread this needle and still conform with compliance. However, in less than one year, PCI 4.0, a revised compliance requirements document, will become effective, creating a major disruption to the IT and Security teams operating contact centers. Primarily, it enforces MFA for just about every access request, which creates its own problems, and although Requirement 8 won't be enforced until March 2025, implementing the necessary solutions should not wait. One of the other areas where security and compliance are about to become dramatically more difficult to satisfy is password management, which we’re going to talk about here.
With BPOs largely servicing customers who are outsourcing their customer service, they will predominately be subject to the requirements as they pertain to third parties, which means agents will see an increase in password rotations for systems and applications owned by their clients. This includes things like CRMs and other client-owned applications.
This poses some challenges for both the BPO and its customers. One result of this requirement is that when agents forget their password after a rotation, they will call the customer's helpdesk to initiate a password reset.
The new password policy requirements are as follows:
8.3.6 If passwords/passphrases are used as authentication factors, they meet the following
minimum level of complexity:
A minimum length of 12 characters (or IF the system does not support 12 characters, a minimum length of eight characters).
Contain both numeric and alphabetic characters.
8.6.3 Passwords/passphrases for any application and system accounts are protected against
misuse as follows:
“ Best practices are to consider password changes at least once a year, a password/passphrase length of at least 15 characters, and complexity for the passwords/passphrase of alphanumeric characters, with upper- and lower-case letters, and special characters.”
This means organizations will rotate once a year rather than once a quarter.
If you’re not already implementing complex passwords, this will be a major lift to get all your systems to implement the change and have all your users reset their credentials to meet the new standards. The bad news is that this process will almost certainly result in a heavy IT workload over the following few weeks, spiking credential resets as users struggle to adapt.
The good news, however, is that once the initial flood of helpdesk tickets dies down, the relaxed rotation period of one year will probably result in a 75% reduction in credential resets at the helpdesk over time. If you stagger the rotation period across your users, you can avoid another huge peak in ticket loads next year when everyone’s credentials reset at the same time, and the new complex passwords drive up locked accounts again. We recommend getting started on this early and rolling it out to users' tranches over a year.
There is an extra sub-requirement for credentials for outsourced call centers and business process outsourcing (BPOs) specifically.
8.3.10.1 Additional requirement for service providers only: If passwords/passphrases are used as the only authentication factor for customer user access (i.e., in any single-factor authentication implementation) then either:
Passwords/passphrases are changed at least once every 90 days, [...]
[...] OR The security posture of accounts is dynamically analyzed, and real-time access to resources is automatically determined accordingly.
While this may be a pain… it gets logistically worse. In the infrastructure of BPOs, often, for reasons outside its control, agents need to have single-factor (password only) access to the customer’s infrastructure. This is protected with VPN tunnels, Citrix, and a host of other technologies, but sometimes it just has to be this way. However, PCI DSS v4.0 places the burden of responsibility for awareness, notification, enforcement of, and therefore liability for, credential rotation on the BPO.
8.3.10 Additional requirement for service providers only: If passwords/passphrases are used as the only authentication factor for customer
user access to cardholder data (i.e., in any single-factor authentication implementation), then guidance is provided to customer users including:
- Guidance for customers to change their user passwords/passphrases periodically.
- Guidance as to when, and under what circumstances, passwords/passphrases are to be changed.
This means things will be tricky in those environments where BPO agents are authenticated into customer infrastructure with a username and password only. The Password requirements remain the same, complex, but rotated. This change will also almost certainly be painful for both BPOs and BPO customers as credential resets mount, and the customer will feel the impact. There is, however, a way around this:
If you can show auditors that you’re dynamically assessing identity risk in real-time, you’ll be allowed to relax rotation to once a year. According to NIST 800-207 Zero Trust Architecture, a dynamically analyzed security posture is a continuous and real-time evaluation of an organization's security risk posture. This means an organization's security posture is assessed automatically and in real-time based on various factors such as user behavior, system configurations, network traffic, and threat intelligence.
Twosense Continuous Multi-Factor Authentication does exactly this. Twosense’s cloud-based machine learning platform analyzes the passive biometric data to learn who your users are, creating a unique profile for each user. Whenever a user passes an MFA challenge, each model continues to learn and adapt to changing behaviors. The more behavior is observed, the more confident Twosense can be that the user is who they claim to be. When the model is mature, Twosense can validate the user's identity and create a baseline of trust.
With Continuous MFA, the user’s recent behavior is continually and automatically analyzed compared to their behavioral biometric model. This means that multifactor checks are being performed on the user continuously throughout the day instead of waiting for the moment the user is authenticating to an application. This is how Twosense is able to meet the requirement of “ having the security posture of accounts dynamically analyzed and real-time access to resources be automatically determined accordingly.” With this requirement met, you can relax credential rotation schedules to annual. Most BPOs have high employee turnover, so you might rarely need to rotate a password, and only for your best employees if you can thread this needle right.
Ultimately, for BPOs looking to mitigate the responsibility of having to request every 90 days that their customer rotate their agent's passwords, Continuous MFA is a must-have solution in its technology stack.
Conclusion
Contact centers face a difficult challenge ahead when it comes to implementing PCI DSS v4.0. With less than a year before PCI DSS v3.2.1 is retired and v4.0 takes effect on March 31, 2024, it is crucial that BPOs are proactive in creating a plan now to ensure compliance is met in time. Despite Requirement 8 being future-date, it is in the BPO’s and its customers’ best interest to begin preparations to meet the new standards before the required implementation date.
The changes made to PCI v4.0 increase scrutiny of BPO security. In addition to increases in MFA across the CDE, v4.0 places the responsibility on the BPO to ensure its customers rotate agents’ passwords every three months –unless certain new requirement conditions are met– and cracks down on mandatory timeouts after 15 minutes of inactivity.
These changes will be extremely challenging to manage and will become increasingly complex to overcome without the proper security partner. Fortunately, Twosense’s one-of-a-kind software will make it a non-issue for BPO contact centers.
Twosense Continuous Multi-Factor Authentication is uniquely designed software for contact centers that does not require a mobile device, hard token, or additional training. Continuous MFA can be deployed as an agent on each user’s machine–deployment is as simple as three easy steps that can be done in a single afternoon.
By implementing Continous MFA, BPOs set themselves apart from their competitors by offering best-in-class service and an elite security experience. Continuous, behavioral biometric authentication provides BPOs and their customers with the frictionless PCI-compliant identity security they have been looking for.
