A White Paper to Fully Passwordless
Access in Hospitals
Table of Contents
- Executive Summary
- Why Identity Security is So Hard in Hospitals
- Shared Workstations Are Inevitable
- Pass-Through Authentication Creates Inherited Risk
- Failed Logins = Delayed Care
- The Impact on Clinical and Security Teams
- For Clinicians
- For Security and IAM Teams
- The Path to True Passwordless
- How the Continuous Authentication and Continuous Access Evaluation Platform Works
- Continuous Authentication as a Security Factor
- Quick Guide to Passwordless in Hospitals
- Deployment at a Major Hospital System
- Key Outcomes
- Real Passwordless Access
- Reduced Clinical Login Failures
- Security Without Workflow Impact
- Why It Matters: Focus on Patients, Not Passwords
- Conclusion: A Path Forward for Hospital Identity
1. Executive Summary
In 2020, one major U.S. healthcare system moved to a 16-character password requirement for all clinical and non-clinical staff. The intention was clear: strengthen security. The reaction was immediate: frustration, login errors, and a surge of help desk tickets. There was a revolt against long, complex passwords, but in hospitals, the options for authentication are limited. Staff complained about having to remember and accurately type long strings under pressure, often making mistakes that locked them out of critical systems.
The policy could not be undone, security demanded it, but leadership recognized the impact on workflows and morale. The search began for a better way. Passwordless authentication was the goal, but any viable solution had to meet strict requirements: remove long passwords, support multiple authentication paths for different groups, provide instant identity verification, and avoid disrupting familiar login experiences.
Hospitals face a unique and often overlooked identity security challenge. Clinical environments are fast-paced, high-stakes, and built around shared infrastructure, not individual devices. The systems used to protect those environments often do the opposite: they slow care, introduce friction, and lead to risky workarounds.
Most healthcare identity solutions, including MFA, badge-based logins, and even Pass-Through Authentication (PTA), weren’t designed for how clinicians actually work. Instead, they create invisible bottlenecks at the worst possible times when seconds matter most. Complex passwords, session timeouts, and inherited trust across shared workstations compromise both security and care delivery.
This white paper examines how these goals can be achieved without compromising care delivery. It examines and explains the limitations of traditional authentication in hospitals, the risks associated with pass-through authentication, and how Continuous Authentication delivers a truly passwordless experience that operates invisibly in the background. Through real-world examples and a major hospital case study, we show how this behavior-based, software-only solution secures every session, protects healthcare systems workflows, and returns valuable time to patient care.
2. Why Identity Security is So Hard in Hospitals
2.1 Shared Workstations Are Inevitable
In hospitals, clinicians are constantly moving between shared terminals in patient rooms, nurse stations, and operating rooms. In these environments, traditional identity solutions quickly break down. Most assume a fixed user-to-device relationship, but in hospitals, that assumption fails instantly. Every workstation will be used by dozens of clinicians in a single day, sometimes within the same hour.
The consequences of this mismatch are significant. Clinicians are forced to log in repeatedly across workstations. When session timeouts are short, which they often are for compliance reasons, users may reauthenticate dozens of times per shift. Each instance pulls attention away from care. Over time, this builds frustration, slows workflows, and contributes to burnout.
More critically, long, complex passwords and repeated re-authentications tend to drive users towards unsafe behaviors. To avoid wasting time, staff may leave sessions unlocked or share passwords with colleagues to ensure quicker access. These aren’t malicious acts; they’re attempts to preserve momentum in an environment where every delay affects patients. But the result is weakened security, unreliable audit trails, and increased exposure to insider threats, fraud, and other external threats.
Shared workstations are here to stay. Any viable identity solution must acknowledge and embrace that reality, rather than fighting against it.
2.2 Pass-Through Authentication Creates Inherent Risk
Pass-Through Authentication (PTA) is commonly deployed in hospital settings because it appears to simplify logins. Once a user authenticates, that “trusted” session can be extended across downstream systems without requiring further prompts. On paper, it sounds ideal: fewer login interruptions, centralized control, and support for regulatory requirements.
Hospitals typically choose PTA for one or more of the following reasons:
- Cloud-first identity models like password hash sync or SSO via SAML are incompatible with their compliance requirements
- They need tight control over credential management for clinical staff and contractors across multiple locations
- Shared workstations and federated identity models complicate the enforcement of authentication policies
- They want to layer MFA or conditional access on top of local controls without exposing credentials to the cloud
PTA is often chosen because it appears to simplify logins and centralize control, but it comes with two critical flaws. The first is exposure: pass-through methods still depend on replaying or storing credentials behind the scenes. If a single endpoint is compromised, such as a malicious USB drive, an attacker can capture the stored credentials and gain access to multiple systems. Instead of containing the threat in this instance, PTA amplifies it.
The second flaw is inherited trust. PTA performs one check at the start of a session, then assumes the same user is still in control, as that trust is extended downstream. In static office environments, this may hold, but in hospitals, it fails immediately. Shared workstations, constant user turnover, and unattended terminals mean PTA cannot tell if the person at the keyboard is still the authorized clinician. Trust is extended downstream without verification, resulting in a loss of identity assurance.
Hospitals don’t operate like offices; every second counts, and every delay can impact patient outcomes. In PTA-enabled environments, the login and access flow typically looks like this:
- A clinician begins their shift with a badge tap + password login

- PTA authenticates the user against the on-prem domain and grants access to the primary session and all downstream apps
- For the rest of the shift, the clinician uses badge taps alone to resume sessions or access shared workstations—no password required
- PTA continues to “pass through” the original trust, copying that login context to any application or endpoint they access
This system is designed for speed, but not for identity security. When a clinician leaves a workstation without logging out, anyone can resume the session, and they inherit the same access. This happens more often than most security leaders are willing to admit. Whether it's during a handoff, a break, or an emergency callaway, sessions are left open, and identity assurance is lost.
2.3 Failed Logins = Delayed Care
Ask any hospital IT team about authentication issues, and they’ll point to failed logins as a major source of support tickets and clinician frustration. Ask the clinicians themselves, and they’ll tell you what it really costs: time with patients.
Hospital workflows demand speed, accuracy, and rapid context switching. Yet, most authentication solutions rarely support that. Complex passwords, MFA prompts, and timeout policies may be effective on paper, but when implemented in hospitals, they interrupt the delivery of care.
Imagine a nurse rushing to a terminal to administer medication, only to be locked out. Or a physician preparing for rounds who loses access to the EHR after a timeout. These interruptions aren’t rare; they happen multiple times per day, per user, and each delay adds up.
According to internal data from a leading U.S. hospital, failed login attempts were occurring at a rate that resulted in both clinical inefficiencies and morale issues. The IT team was flooded with password reset requests and access issues. Meanwhile, clinicians began avoiding certain workstations or relying on colleagues to stay logged in, exposing the organization to security risk.
When authentication fails, patient care suffers. Identity tools shouldn’t just protect systems; they should support the people who deliver care.
3. The Impact on Clinical and Security Teams
3.1 For Clinicians
Clinicians are trained to act quickly and in the best interest of their patients. But when security friction gets in the way, clinicians are forced to navigate obstacles that don’t improve outcomes, but delay them.
Long, complex passwords and repeated re-authentications introduce friction that accumulates throughout a shift. In clinical environments, even brief interruptions can derail workflows. Charting is paused, medication is delayed, communication is disrupted, and over time, this friction leads to clinician burnout. When authentication becomes a roadblock, everyone loses: clinicians, IT, but most importantly, patients.
3.2 For Security and IAM Teams
Security and identity leaders in healthcare face a tricky balancing act: protect sensitive systems while enabling workflows that demand speed and flexibility. However, in practice, this often means making compromises. If security were the sole factor, IT would implement stricter controls; however, this leads to increased friction. The flip side is relaxing policies to avoid disrupting care, which ultimately compromises security—a trade-off that is wholly unacceptable for hospitals.
PTA and traditional MFA offer partial solutions, but create more problems in shared environments than they resolve. Once a user is authenticated, the session is trusted even if someone else takes over. This undermines auditability, exposes sensitive data, and violates the principle of least privilege.
Meanwhile, managing password policies, lockouts, and badge access systems adds overhead to already overstretched IAM teams. Help desk staff are stuck endlessly resetting passwords. Security teams often lack visibility into real-time user behavior, and incident investigations are complicated by the unreliability of logs.
Without a way to continuously verify who is behind the keyboard, security teams are left relying on the hope that the right person is still using the session.
4. The Path to True Passwordless
Twosense replaces static, front-loaded authentication with continuous, real-time identity verification that runs invisibly in the background.
4.1 How the Continuous Authentication and Continuous Access Evaluation Platform Works
Continuous Authentication fundamentally shifts the paradigm of identity security and how it is verified. Instead of checking once at login and assuming trust, the Continuous Authentication and Continuous Access Evaluation platform silently, continuously, and without requiring user input, monitors identity throughout the entire session.
Twosense achieves this through behavioral biometrics. Every user has unique patterns in how they type, move the mouse, and interact with a system. These subtle behavioral signals form a biometric “fingerprint” that can’t be faked or shared.
A lightweight software agent runs on shared workstations, monitoring these behavioral signals and comparing them to each user’s trust profile. If the behavior aligns, the session continues seamlessly; if it doesn’t, if someone else takes over or behavior changes, the session is flagged or terminated.
Continuous Authentication enables real-time, session-aware identity assurance. There are no phones, no cameras, no tokens, and no need for clinicians to learn new workflows. It’s invisible by design, and that’s what makes it powerful.
4.2 Continuous Authentication as a Security Factor
Traditional authentication relies on static credentials, one-time factors, or pass-through trust. Once access is granted, identity is assumed. Continuous Authentication changes this by turning behavior into a persistent security factor. By combining Continuous Authentication, the Continuous Access Evaluation Profile (CAEP), and a policy-driven Orchestration Engine, Twosense delivers real-time, session-aware identity assurance.
Instead of replaying stored credentials or extending trust based on an initial login, Twosense uses behavioral biometrics as an active authentication factor. Typing rhythm, keystroke cadence, and mouse movement form a live, session-based biometric signature, something unique to each individual and impossible to share, steal, or replicate.
This behavioral identity factor can be directly tied to the hospital's authentication policy. That means IAM teams can set conditions such as:
- Sessions that remain consistent with the user’s behavioral profile are automatically authorized.
- Sessions that diverge significantly are flagged, escalated, or terminated.
- Unauthorized users cannot gain access simply by taking over an open workstation.
CAEP shares trust signals with connected systems in real time, eliminating blind spots between login and logout. The Orchestration Engine converts those signals into immediate action, triggering re-authentication or session termination when trust no longer meets policy.
This ensures that a clinician logging into a shared workstation is recognized immediately and allowed to continue working without interruption, while an unauthorized user attempting to access the same session is blocked in real-time.
Continuous Authentication doesn’t just strengthen policy enforcement; it integrates directly into the hospital’s existing security infrastructure. Alerts and remediation actions can be integrated into existing workflows, ensuring that any unauthorized use is promptly detected, escalated, and contained.
The result is an authentication model that adapts to the fluid, shared, and high-stakes environment of hospitals. Clinicians experience frictionless, automated access. Security teams gain session-level assurance. And hospitals finally achieve passwordless authentication that doesn’t rely on pass-through authentication.
4.3 Quick Guide to Passwordless in Hospitals
Hospitals do not need a full identity overhaul to go passwordless. A Top 10 U.S. health system succeeded by starting small and scaling fast with a practical, repeatable approach that enables hospitals to move to passwordless access without disrupting care:
Step 1: Start With One High-Touch App
Begin with the applications that generate the most login friction—EHR, pharmacy, or radiology systems. Early wins demonstrate impact and build internal momentum.
Step 2: Automate Login With Continuous Authentication
Deploy Twosense Continuous Authentication to run silently in the background, verifying identity in real time. No phones, tokens, or new workflows are required.
Step 3: Reduce Password Use Immediately and Automatically
Clinicians stop entering passwords, failed logins drop, and help desk tickets decline. Identity is verified continuously and automatically.
Step 4: Expand to Your Core Clinical Apps
Once the first application is passwordless, apply the same model to additional high-touch clinical apps. Scale incrementally without disrupting workflows.
Step 5: Continue Scaling Toward Full Passwordless
Repeat the process across the remaining applications and user groups. Establish passwordless access as the standard across the hospital.
.png?width=980&height=588&name=Scaling%20with%20Twosense-9%20(1).png)
4.4 Deployment at a Major Hospital System
In late 2024, one of the largest hospital systems in the United States faced a growing problem: its authentication systems were contributing to clinical burnout and operational inefficiencies. The organization had implemented a 16-character password policy to improve security. Still, the result was chaos: constant login failures, frustrated staff, and a flood of help desk tickets, with a senior team member going so far as to state that there was a “revolt.”
Clinicians were caught between rigid identity policies and the realities of care delivery. Phone-based MFA didn’t work in sterile areas or environments with PPE. Pass-through authentication was ruled out due to its inherent security risks, including a lack of session awareness, storing unhashed passwords, and the potential for inherited access.
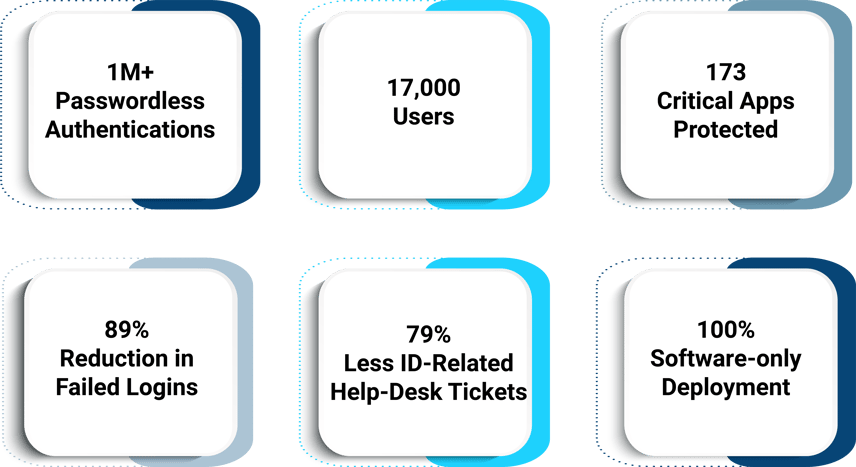
The hospital partnered with Twosense to implement Continuous Authentication across 17,000 users and 173 clinical applications. The deployment required no new hardware, no retraining, and no changes to the existing infrastructure.
Within six months:
- 1M+ passwordless logins were completed
- Failed login attempts dropped by 89%
- Login-related help desk tickets decreased by 79%
Continuous Authentication Platform Results in a Leading U.S. Hospital
Most importantly, clinicians noticed the difference. They began looking for Twosense-enabled workstations, knowing they would experience fewer interruptions and smoother shifts. The technology didn’t just improve security; it improved morale.
5. Key Outcomes
5.1 Real Passwordless Access
Twosense delivers on the promise of passwordless identity not by copying trust across sessions, but by verifying identity throughout them. Unlike PTA, which blindly extends login approval, Continuous Authentication ensures that every session remains secure in real time. Clinicians don’t need to enter or manage long, complex credentials or respond to prompts. The system recognizes them based on how they work, allowing them to focus entirely on care.
5.2 Reduced Clinical Login Failures
By eliminating passwords and automating authentication, Twosense dramatically reduces the rate of failed logins. In the hospital case study, "Reducing Clinician Burnout and Improving Patient Care With Continuous Authentication," failed clinical logins dropped by nearly 90%.
This improvement had ripple effects across the organization. Fewer help desk calls meant IT teams could focus on higher-value tasks. Fewer interruptions meant clinicians could spend more time at the bedside. And fewer login failures meant less frustration, fewer delays, and faster care delivery.
5.3 Security Without Workflow Impact
Twosense integrates with existing infrastructure and identity providers. It works with shared workstations and federated environments. This means security is enforced without creating friction or requiring users to learn a few processes. Identity verification becomes part of the background, always on, always being continuously evaluated, and never in the way. For hospitals, this is the sweet spot: stronger security with zero disruption to workflow.
6. Why It Matters: Focus on Patients, Not Passwords
In healthcare, time is the most valuable resource. Every second spent logging in, re-authenticating, or calling the help desk is a second not spent with a patient. Twosense returns time to the people who need it most, clinicians and their patients. It doesn’t just protect identities; it protects workflows, trust, and patient outcomes. It gives clinicians the freedom to move between workstations, systems, and tasks without worrying about security, as it’s already happening invisibly.
This is what modern identity should look like. It should enable clinicians, not burden them. It should support care delivery, not delay it, and it should do all of this without compromising security efficiency.
7. Conclusion: A Path Forward for Hospital Identity
Hospitals can no longer afford identity systems that slow down care, frustrate staff, and leave sessions vulnerable to misuse. Static logins and pass-through models don’t work in environments where users move constantly and share infrastructure.
Continuous Authentication offers a new path, one that secures every session, supports every user, and restores time for clinicians to focus on delivering care. It meets clinicians where they are: fast-moving, focused on patients, and tired of credentials getting in the way.
This isn’t about adding another layer of security. It’s about removing the friction between care and compliance. It’s about protecting the people who protect patients. And it’s already in use today.

